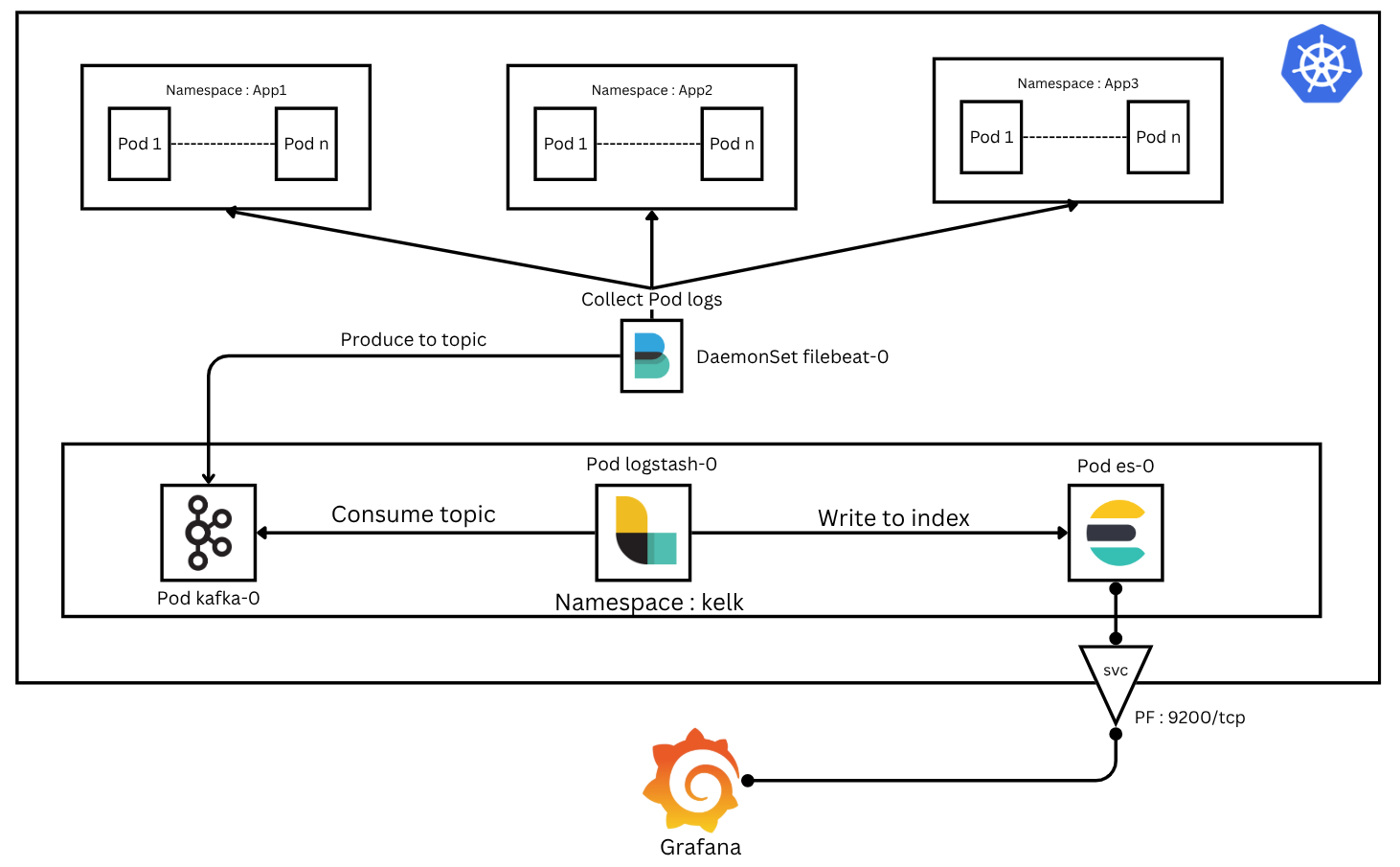
Wazuh Active Response MCP Server - AI Integration in Incident Response
In our recent blog posts, we’ve deployed and built several MCP servers designed to handle critical SOC operations such as alert investigation, threat intelligence, and more. Now, we’re shifting our...